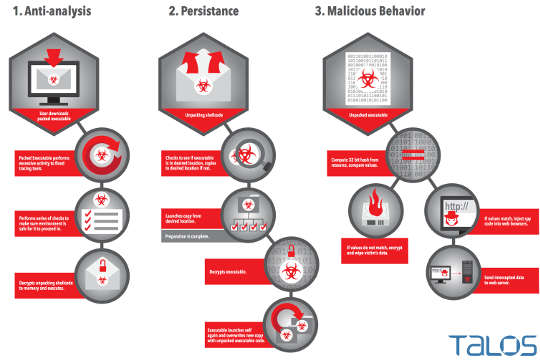
Ben Baker and Alex Chiu, from Cisco Talos, wrote a report on the Rombertik Malware.
Rombertik can erase the disk’s Master Boot Record it resides on, if malware analysis techniques are used.
Summary :
“Threat actors and security researchers are constantly looking for ways to better detect and evade each other. As researchers have become more adept and efficient at malware analysis, malware authors have made an effort to build more evasive samples.
Better static, dynamic, and automated analysis tools have made it more difficult for attackers to remain undetected. As a result, attackers have been forced to find methods to evade these tools and complicate both static and dynamic analysis.
In the process of reverse engineering the Rombertik malware, Talos discovered multiple layers of obfuscation and anti-analysis functionality. This functionality was designed to evade both static and dynamic analysis tools, make debugging difficult. If the sample detected it was being analyzed or debugged it would ultimately destroy the master boot record (MBR)”.