What is a risk assessment?
Risk assessment is a process for identifying:
- Assets of an organization to protect
- Threats to them
- Assets criticality
- Consequences if an asset would be lost or damaged
- Existing Vulnerabilities
- Probabilities of attacks
At the end of this process we express the risks we face and prioritize them. Finally, we recommend countermeasures to reduce those risks.
Why do a risk assessment?
Without a methodical assessment, the security system we design might waste valuable resources on unnecessary protection. Worse, it could fail to protect a critical asset …
Even the most carefully designed security system requires a periodic review. A review can measure the effectiveness of the system and adjust it if the threat environment has changed.
How to do a security risk assessment – The process
1 – Identify Assets
The first step of a risk assessment is to create a comprehensive list of the assets of the organization.
Then determine their criticality, and the consequences if those assets were to be compromised.
There are 4 categories of assets:
- People (employees, customers, contractors, visitors)
- Property (buildings, equipments, supplies, cash)
- Information (secret formula, software, records)
- Reputation
All these assets can be attacked and should be defended.
Risk can only exist against assets.
1.1 – Estimate Assets Criticality
Criticality is the measure of an asset’s importance to the mission of the business.
If the organization cannot operate without an asset, it is said to be critical. Otherwise criticality could be: high, medium, low or none.
Rate assets criticality on a scale of 1 (none) to 5 (critical).
1.2 – Determine Consequences
Risks have consequences.
Consequence is the impact that the loss or damage of an asset could have on the organization.
It could be loss of production, money, reputation, casualties, damaged property, etc …
Assessing consequences is a crucial part of the risk assessment.
Rate consequences for each asset on a scale of 1 (insignificant) to 5 (catastrophic).
2 – Identify Threats
First of all, threats are not hazards. Hazards can be either natural (earthquake) or man-made (work accident). They are generally unintentional or without malice.
Threats are always man-made, intentional and with malice.
A threat actor is an individual or group that has the capability and intent to attack your assets. It is an adversary.
Without a threat actor there is no risk.
There are 5 categories of threat actors :
- Petty criminals – Vandals, Pickpockets, Drunks
- Violent criminals – Deranged person, Rapists, Disgruntled employee
- Economic criminals – Transnational Mafia, Organized crime, Skilled thieves
- Subversives – Spies, Hackers, N.G.O. Activists
- Terrorists – Intelligence service, Religious fanatics, Guerrilla, Amateurs
All these threat actors have different capabilities (knowledge, equipment, weapons) and motivations (money, vengeance, ideology).
3 – Do A Vulnerability Analysis
A vulnerability is a flaw in a system that may allow an adversary to exploit it to gain access to assets.
There is no such thing as a system without vulnerabilities.
A vulnerability analysis should:
- Define attack scenarios and their likely result
- Evaluate the effectiveness of existing security measures
- Identify vulnerabilities
This could be the most technical part of the risk assessment, for a good knowledge of adversary modus operandi and security measures effectiveness is required.
At the end of the analysis, rate the assets vulnerability on a scale of 1 (maximum protection) to 5 (no protection at all).
4 – Estimate Attack Probability
Probability is the likelihood that a threat actor will select and then attack an asset.
For estimating the probability of a criminal attack it is possible to use the statistics published by the local authorities. The data gathered should cover at least the last 5 years.
If no data is available we could estimate the probability of attack by analyzing the assets attractiveness.
What can the adversary gain by attacking the asset?
What is the probability of a successful attack?
What is the probability of capture?
What does the attacker lose if identified/captured?
Rate the probability of attack from a threat actor on a scale of 1 (rare) to 5 (almost certain).
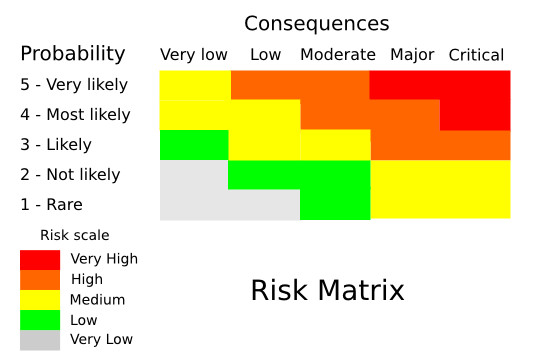
5 – Express The Risks
Perhaps the most famous part of risk assessment. After having gathered all the data, we can now use it to estimate the risk that the assets face.
There are different methods for expressing risk. Most of them take into account the probability of an event happening and its consequences.
A simple formula for expressing risk is:
Risk = Probability x Consequences
This formula however does not explicitly take into account the vulnerability factor.
Another risk formula that is often used:
Risk = Probability x Vulnerability x Consequences
This formula explicitly states that risk is a function of three factors.
The probability of an event happening (an attack by a threat actor in a security risk assessment), our vulnerability to that event, and finally, the consequences of that event.
If we could reduce one factor, we would face a lesser risk.
Since we have been rating these factors on a scale of 1 (very low) to 5 (very high), it would be nice if we could get a risk expression on the same scale.
In order to have that, we can use this formula:
Risk = ( Probability + Vulnerability + Consequences ) / 3
A Quick Example
The probability of script-kiddies (low capabilities hackers) trying to hack into the company’s Internet web server is high. Probability is 4.
The server is properly configured and always quickly updated with the latest security patches. Vulnerability is 1, the adversary does not have the capability to mount a successful attack.
The asset does not host sensitive data and cannot communicate with the company private network. Consequences are 1.
Risk = (4+1+1) / 3 = 2
So in that case, the risk is low.
6 – Prioritize The Risks
Often several assets face the same risk level but not enough resources are available to decrease the risk for all of them.
So how do we choose which asset to protect in priority?
There are many ways to prioritize risk. One could prioritize by probability of attack, criticality of assets or even cost of countermeasures.
A good criteria is consequences. When in doubt, rank assets by consequences. The assets with the highest risks and consequences are the ones you should protect first.
7 – Countermeasures Recommendations
We are reaching the end of the risk assessment, we know which assets to protect, from whom and why. We must now recommend how.
Countermeasures are the security measures we take to decrease the vulnerability of our assets.
To learn more about physical countermeasures, read this article :
Select countermeasures with a cost/effectiveness approach. No point of spending $10 000 for an asset with $1000 consequences …
—
This is the end of the security risk assessment, a very important methodology in designing a security system or reviewing its effectiveness.
It is the basis of a good security program and should not be overlooked.































Good introduction to the risk assessment process. Thanks.
Very useful …
Very neat article. I use the risk matrix for home security.